Labeling Google Cloud Platform resources
Do you run and manage applications on the Google Cloud Platform (GCP)? Do you need to group and classify your GCP resources to satisfy compliance requirements? Does your finance team is asking for visibility on which team is spending where and how? Do you want to track GCP resource utilization by the team and the engineer? If you answered yes to any of these questions, you’ll be glad to know that GCP provides multiple ways to annotate your resources, to make them easier to track, security marks, labels, and network tags.
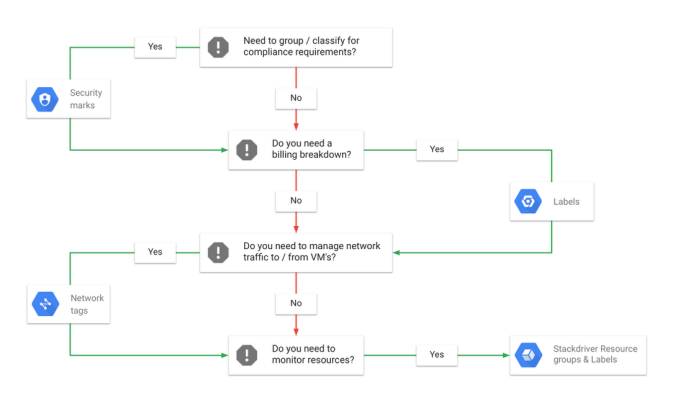
While each annotation has different functionality and scope, they are not mutually exclusive and you will often use a combination of them to meet your requirements. To help you choose which annotation, when, take a look at this flowchart.
Let’s take a deeper look at each of these types of annotations.
Annotation type: Security marks
Security marks, or marks, provide you a way to annotate assets and then search, select, or filter using the mark via Cloud Security Command Center (Cloud SCC)
Use cases:
Here are the main use cases for security marks:
- Classifying and organizing assets and findings independent of resource-level labeling mechanisms, including multi-parented groupings
- Enabling tracking of violation severity and priority
- Integrating with workflow systems for assignment and resolution of incidents
- Enabling differentiated policy enforcement on resources, projects or groups of projects
- Enhancing security-focused insights into your resources, e.g., clarifying which publicly accessible buckets are within policy and which are not
Note that Cloud Labels and Tags for the associated supported resources also appear and are indexed by Cloud SCC, so that you can use automation logic to create/modify marks based on the values of existing resource labels and tags.
How to use:
Marks are key-value pairs that are supported by a number of resources. They provide a security-focused view of the supported resources and are only visible from Cloud SCC. Edit or view access to the inventory of resources in Cloud SCC and their associated marks requires the securityCenter.editor IAM role, independently of the roles and permissions on the underlying resource. You can set marks at the org level, project level or for individual resources that support marks. To work with marks you can use, CURL, REST API, the Cloud SCC python library or the Cloud SCC asset inventory page by selecting the resources you wish to apply a mark to, then adding the key-value pair items.
What you can annotate:
A valid mark meets the following criteria:
- Keys must have a minimum length of 1 character and a maximum length up to 256 characters and value can then have a maximum of 4096 characters.
- Keys and values can contain only lowercase letters, numeric characters, underscores, and dashes. All characters must use UTF-8 encoding and can include international characters.
You can find an up-to-date list of resources that can be annotated using marks here.
Annotation type: Labels
Labels are key-value pairs that are supported by a number of GCP resources. You can use labels to track your spending in exported billing data. You can also use labels to filter and group resources for other use cases, for example, to identify all those resources that are in a test environment, as opposed to those in production.
Here’s a list of all the things you can do with labels:
- Identify resources used by individual teams or cost centers
- Distinguish deployment environments (prod, stage, QA, test)
- Identify owners, state labels.
- Use for cost allocation and billing breakdowns.
- Monitor resource groups via Stackdriver, which can use labels accessible in the resource metadata
How to use:
A valid label meets the following criteria:
- Each label must be a key-value pair.
- Keys must have a minimum length of 1 character and a maximum length of 63 characters, and cannot be empty. Values can be empty and have a maximum length of 63 characters.
- Keys and values can contain only lowercase letters, numeric characters, underscores, and dashes. All characters must use UTF-8 encoding and can include international characters.
- The key portion of a label must be unique. However, you can use the same key with multiple resources. Keys must start with a lowercase letter or international character.
Check the supported resources to learn how to apply labels and to what you can apply them. For instance, BigQuery lets you add labels to your datasets, tables, and views, while Cloud Storage allows you to add labels to buckets. You can add labels to projects but not to folders.
The permissions you need to add labels to resources are determined on a product-by-product basis. For example, BigQuery requires the bigquery.datasets.update permission to modify labels on datasets. The owner of the dataset has this permission by default but you can also assign at the project level the predefined IAM roles bigquery.dataOwner and bigquery.admin, which include this permission. You can also add labels to tables and views; this action requires the bigquery.tables.update permission. Assigning the predefined IAM roles at project level bigquery.dataOwner, bigquery.dataEditor or bigquery.admin grants this permission. The owner of the dataset has full permissions over the tables and views that the dataset contains.
What you can label:
An up-to-date list of GCP products that support labels can be found here. Then, drill down into each product’s documentation for more details.
Note that you can label instances, but if you are annotating these to manage network traffic, you should use tags instead (see below).
Annotation type: Network tags
Network tags apply to instances and are the means for controlling network traffic to and from a VM instance. On GCP networks, tags identify which VM instances are subject to firewall rules and network routes. You can use the tags as source and destination values in firewall rules. For routes, tags are used to identify to which instances a certain route applies.
How to use:
Using tags means you can create additional isolation between subnetworks by selectively allowing only certain instances to communicate. If you arrange for all instances in a subnetwork to share the same tag, you can specify that tag in firewall rules to simulate a per-subnetwork firewall. For example, if you have a subnet called ‘subnet-a’, you can tag all instances in subnet-a with the tag ‘my-subnet-a’, and use that tag in firewall rules as a source or destination.
Tags can be added or removed from an instance using gcloud commands, Cloud Console or API calls. The following gcloud command will add the tags ‘production’ and ‘web’ to an instance
| gcloud compute instances add-tags [INSTANCE_NAME] –tags production,web |
You can set firewall rules using gcloud commands and the Console. The following gcloud command sets a firewall rule using tags in the source and destination. It allows traffic from instances tagged web-production to instances tagged log-data via tcp port 443
| gcloud compute firewall-rules create web-logdata –network logging-network –allow TCP:443–source-tags web-production –target-tags log-data |
For routes, tags are used to identify which instances a certain route applies to. For example, you might create a route that applies to all VM instances that have been tagged with the string VPN. You can set routes using gcloud commands or the Console. The following gcloud command creates a route called my-route in a network called my-network that restricts the route to only apply to instances tagged ‘web-prod’ or ‘api-gate-prod’.
| gcloud compute routes create my-route –destination-range 10.0.0.0/16 –network my-network [–tags=web-prod,api-gate-prod] |
Network tags can, however, be modified by anyone in your org who has the Compute InstanceAdmin role in the project the network was created in. You can create a custom role with more restricted permissions that disable the ability to set tags on instances by removing the compute.instances.setTag permission from the Compute InstanceAdmin role. Instead of using tags and custom roles to prevent developers from adjusting tags (and thus enabling a firewall rule on their instances), use service accounts; Unless they have access to the appropriate centrally managed service accounts they will be unable to modify the rule. Refer to service accounts vs tags to determine whether the restrictions when using service accounts for firewall rules are acceptable.
Tags values have to meet the following criteria:
- Can be no longer than 63 characters each
- Can only contain lowercase letters, numeric characters, and dashes
- Must start and end with either a number or a lowercase character.
Marks, labels and network tags at a glance
To recap, here’s a table that summarizes common use cases and their associated annotations.
Use Case | Annotation(s) required | Notes |
Taking inventory of GCP resources | Security marks Labels | Labels currently support a wider range of resources than Security marks. The Cloud SCC view of your resources includes, as properties of the resource, the labels and tags you’ve applied; you can then further apply ACL’d security marks to control the organization and filtering of the superset of resources, tags and labels. |
Classifying or grouping GCP resources and data into logical groups such as dev or production environments for non-ACL’d use cases | Labels | |
Classify or grouping GCP resources and data into logical groups such as dev or production environments for security use cases | Security marks | Use these when you want the control of the groups to be at either an organization level or specifically not in the control of the resource owner. |
Grouping and classifying sensitive resources and/or organize resources for attribution in security use cases | Security marks | Reading & setting marks is restricted to the Cloud SCC specific roles |
Billing break down and cost allocation | Labels | |
Network traffic management to and from instances | Tags | Network tags can be modified by anyone in your org who has the Compute InstanceAdmin role |
Monitoring groupings of related resources for Operational tasks | Labels | Used with Stackdriver resource groups |
Monitoring of groupings of related resources and/or findings for security risk assessments, vulnerability management, and threat detection | Security marks | Used in Cloud SCC |
On your mark, get set, go
If you manage a big, complex environment, you know how hard it can be to keep track of all your GCP resources. We hope that security marks, labels and network tags can make that task a little bit easier. For more information on tracking resources in GCP, check out this how-to guide on creating and managing labels. And watch this space for more insider tips on managing GCP resources like a pro.
Sourced from Google Cloud Platform blog by Grace Mollison